Agent Communications Language or FIPA-ACL. It looks and acts much like a regular computed field but has some extra parts that do some extra work.

What Is Access Control List Acl Types Linux Vs Windows Imperva
An IBM protocol used in airline reservations systems such as American Airlines SABRE System and United Airlines APOLLO.

Acl definition computer. Short for access control list a set of data that informs a computers operating system which permissions or access rights that each user or group has to a specific system object such as a directory or file. Austin City Limits a television show. These operations typically include read write and execute.
Asynchronous Connection-Less Bluetooth protocol. Short for discretionary access control list DACL is a single ACL containing permissions of what users and groups can access. ACLs are used to filter traffic based on the set of rules defined for the incoming or out going of the network.
It defines what users and groups can access the object and what operations they can perform. The list has an entry for every user with access rights to the system. The ACEs are used by an operating system or another network device to appropriately restrict the rights users have.
ACL Stands For. 04262017 by Computer Hope. Access-control list in computer security a list of permissions for accessing a computer system resource.
Access-list ACL is a set of rules defined for controlling the network traffic and reducing network attack. An Access Control Lists ACL is a function that watches incoming and outgoing traffic and compares it with a set of defined statements. In ACL a conditional computed field CCF is basically a regular computed field with some fireworks.
In the computer networking world an ACL is one of the most fundamental components of security. Each object has a security property that connects it to its access control list. ACE ACL Computer acronyms Security terms.
In a Microsoft context the Access Control List ACL is the list of a system objects security information that defines access rights for resources like users groups processes or devices. An access control list ACL is a table that tells a computer operating system which access rights each user has to a particular system object such as a file directory or individual file. For example an ACL may specify if a user has access to a file or folder on that computer or network.
Stands for Access Control List An ACL is a list of user permissions for a file folder or other object. The access control entries present in access control lists control all the access to the associated objects from the users or programs that would want to use them. The network routers are given a list of rules called an access control list ACL that can permit basic admission to or from a network segment as well as the permission to access services that may be available through them.
The system object may be a file folder or other network resource. They define who and at what level can the object or resource be used by entities. ACL software company formerly Audit Command Language.
Short for access control list an ACL is a list containing one or more ACEs Access Control Entries. Both ALC and P1024B the Unisys version employ a de facto standard six-bit coding scheme. A filesystem ACL is a table that informs a computer operating system of the access privileges a user has to a system object including a single file or a file directory.
Each object has a security attribute that identifies its access control list. Fortunately the extras are NOT complicated and after reading this post you will find that will you use CCFs frequently. ACL access control list.
Access control list A set of data associated with a file directory or other network resource that defines the permissions that users. Austin City Limits Music Festival. Access Control List Agent Communication Language Asynchronous connectionless Link Agent Communication Library Asynchronous Connection-Less Average Call Length Access Control List Corel Draw 6 Keyboard Accelerator Microsoft Office.
Akar-Bale language an extinct Great Andamanese language ISO 639-3 code ACL. Access rights ACE ACS. See also coding scheme standard and protocol.
What Is The Difference Between Access Control List And Access Control Matrix Pediaa Com
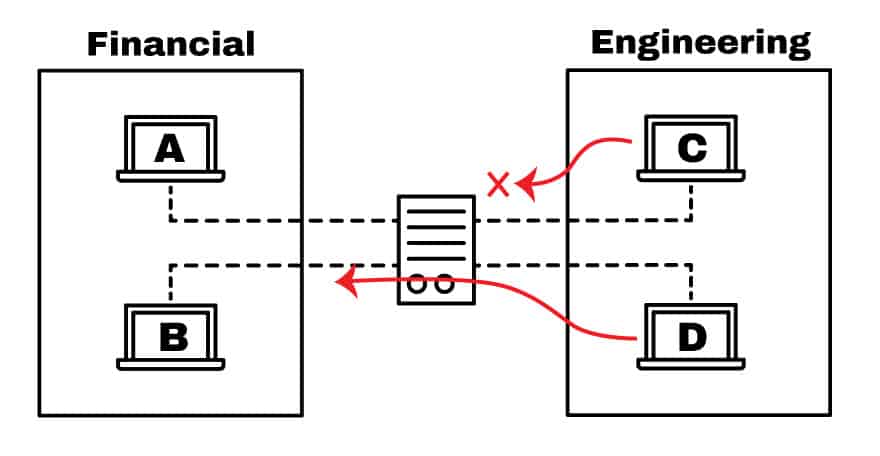
Access Control List Acl What Are They And How To Configure Them Itt Systems
What Is Acls Error Solutions To Acls Errors Examples
%20preview.jpg)
Access Control List Acl What Is Types Where To Place

Access Control List Explained With Examples

Tentang Dokumen Acl Binekas S Blog
What Is An Access Control List Acl What Is An Access Control List Acl Huawei

Teknik Audit Berbantuan Komputer Menggunakan Software Acl For Windows Ppt Download

Configure Standard Access Control List Step By Step Guide
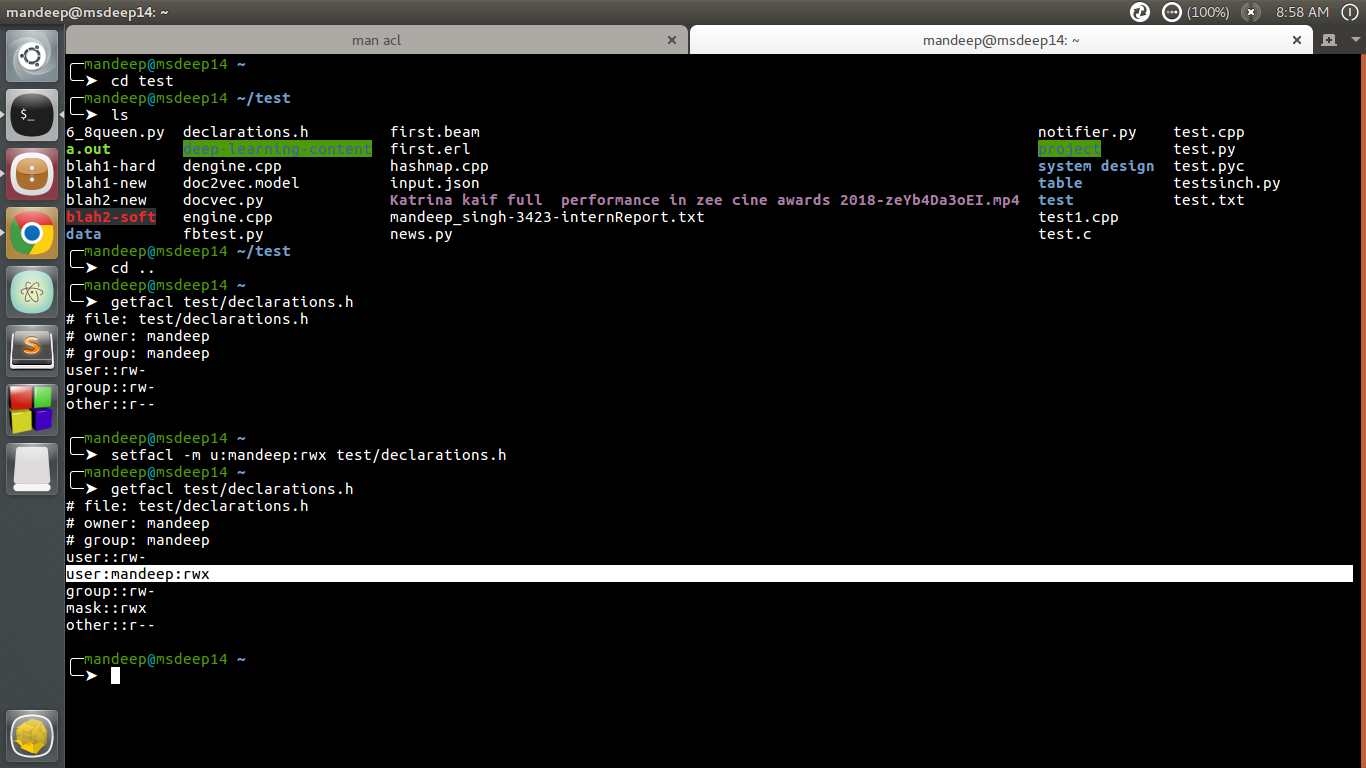
Access Control Lists Acl In Linux Geeksforgeeks

Configure Standard Access Control List Step By Step Guide

Access Control List Acl What Are They And How To Configure Them Itt Systems

Access Control List Explained With Examples
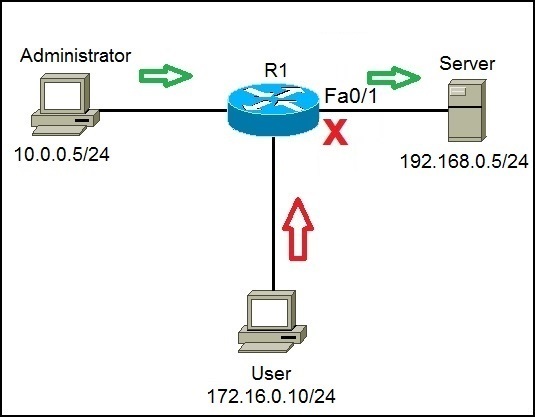
What Is Acl Access Control List Ccna

Access Control Lists What Are Them And How To Configure

Configure Standard Access Control List Step By Step Guide
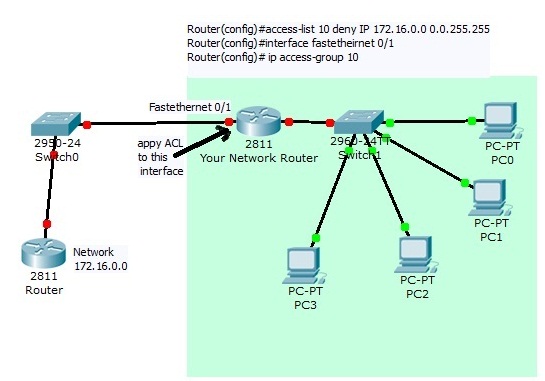
Access Control List Configuration On Cisco Router Securitywing

Access Control List Acl What Is Types Where To Place

Standard Access List Geeksforgeeks
No comments:
Post a Comment